Ichidoku
With the right tool, your cyber-physical network will be transparent
Industrial Control Systems (ICS) and critical infrastructures (a subgroup of ICS) were often built in an era when sophisticated malware attacks did not exist, or at least they were not common. These threats are real now and many systems still fail to catch up with them.

ICHIDOKU'S MAIN GOAL
What does it do?
Ichidoku makes your cyber-physical network transparent. Patchwork OT will be visible and you will have a clear understanding of how your system is built - this gives you the knowledge to defend yourself against attacks. It also reduces vendor-dependency. It is specifically designed for industrial sized systems, incl. critical infrastructures.
A lot of different protocols are used, and Ichidoku can adapt to each system and handle even the unique ones. Ichidoku works with network data, in a passive manner, so the original system can work undisturbed. Also, an integrated vulnerability database helps to detect vulnerabilities, anomalies and cyber security incidents automatically or based on the rules you gave.
tools in the box
Product features
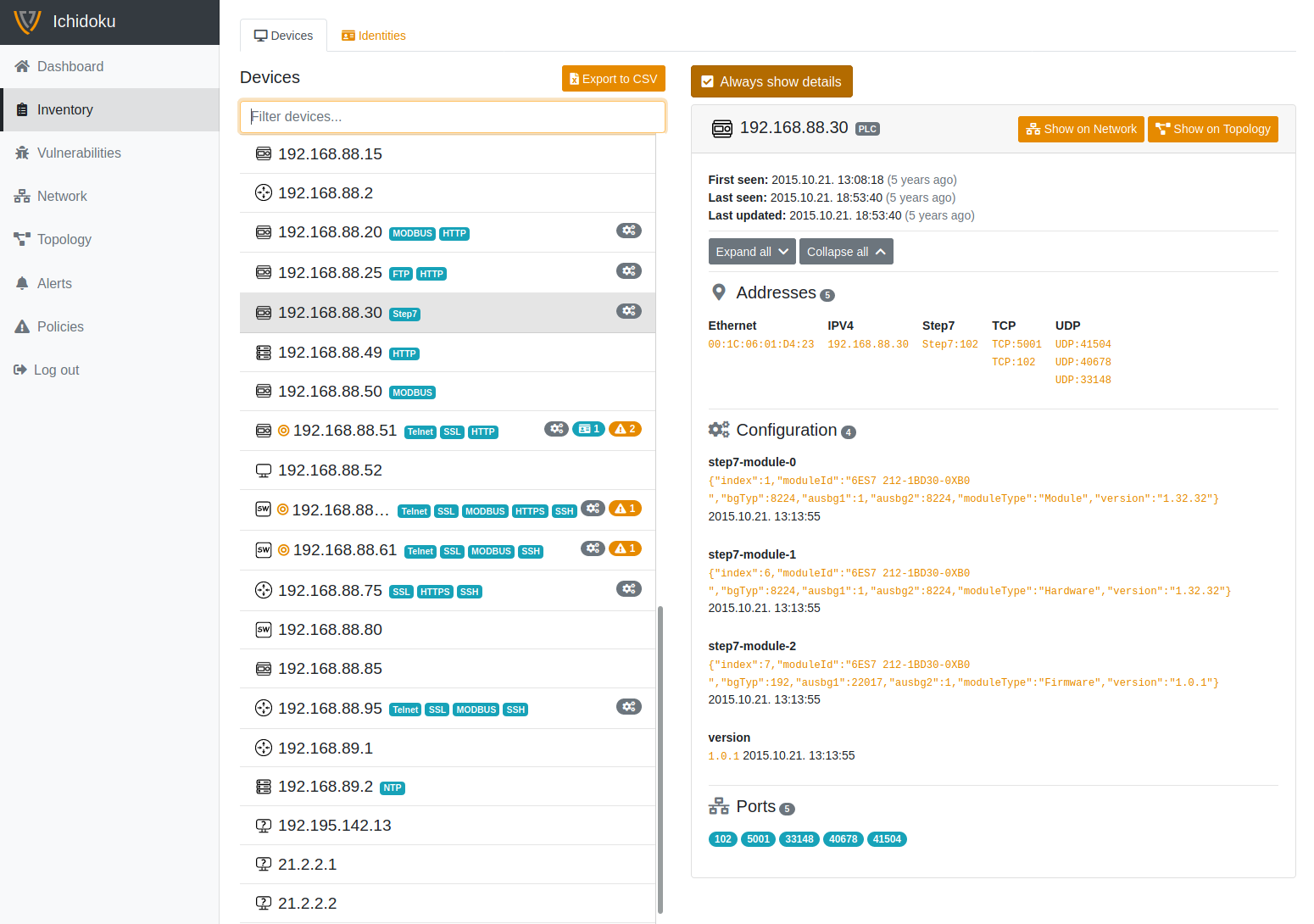
Autodiscovery and inventory
Ichidoku can automatically discover all the assets communicating in your industrial network, it runs on a real time working system - without interfering production. You will get all the necessary information of existing ports, protocols and machines to prepare a thorough defence plan, with all just a few clicks, therefore even experts with less OT experience can fully benefit from it.
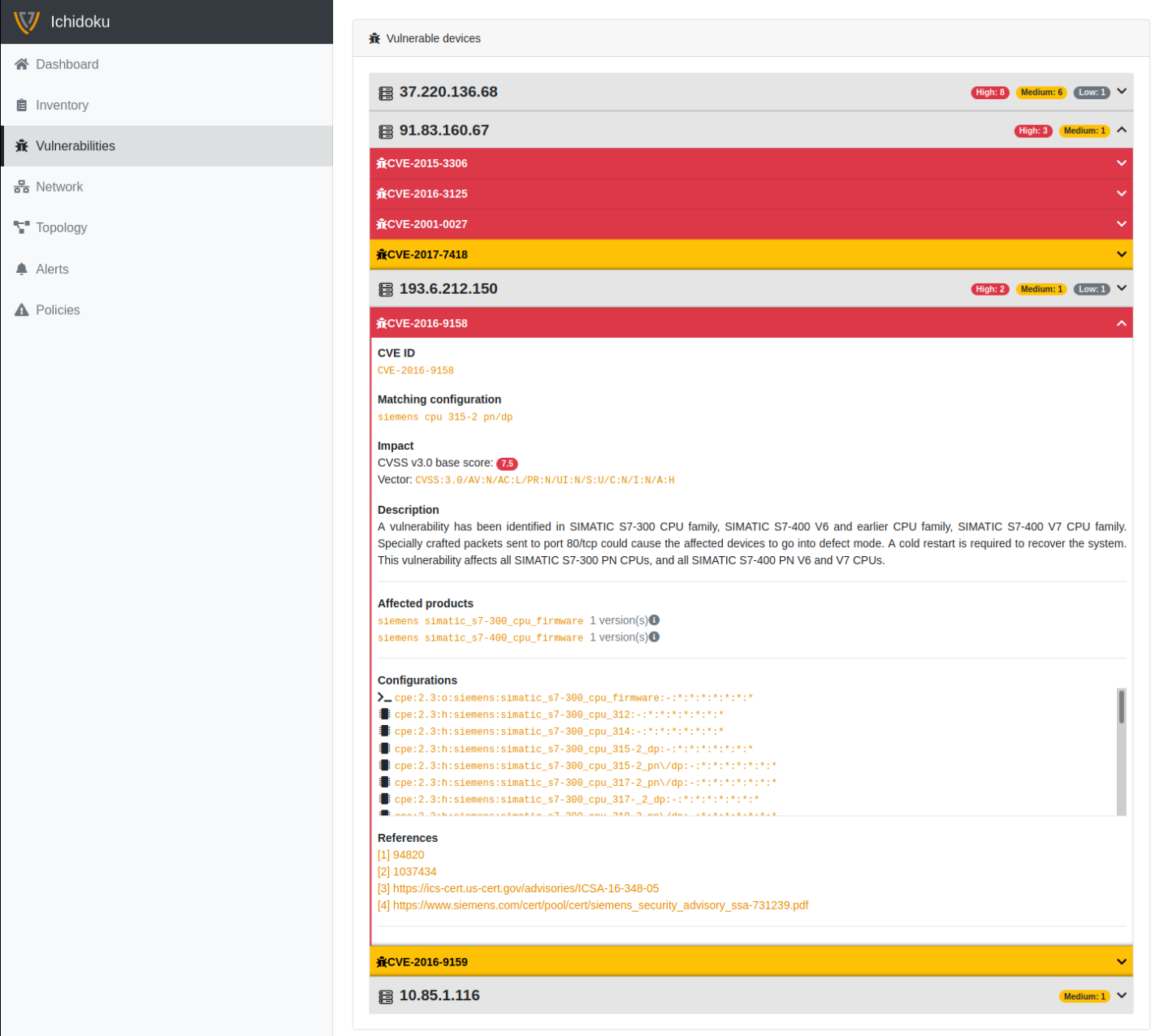
Common Vulnerabilities and Exposures (CVE) database
Once you know what assets you have, you probably also want to know their vulnerabilities, but vulnerability scan is a tricky business even in an IT environment, let alone in OT. Unexpected data traffic from vulnerability scan can cause trouble, systems might crash and operation might stop. Ichidoku comes with a built-in vulnerability database and will highlight potential risks in your network. This activity also does not generate data traffic and will not interfere with operation flow.
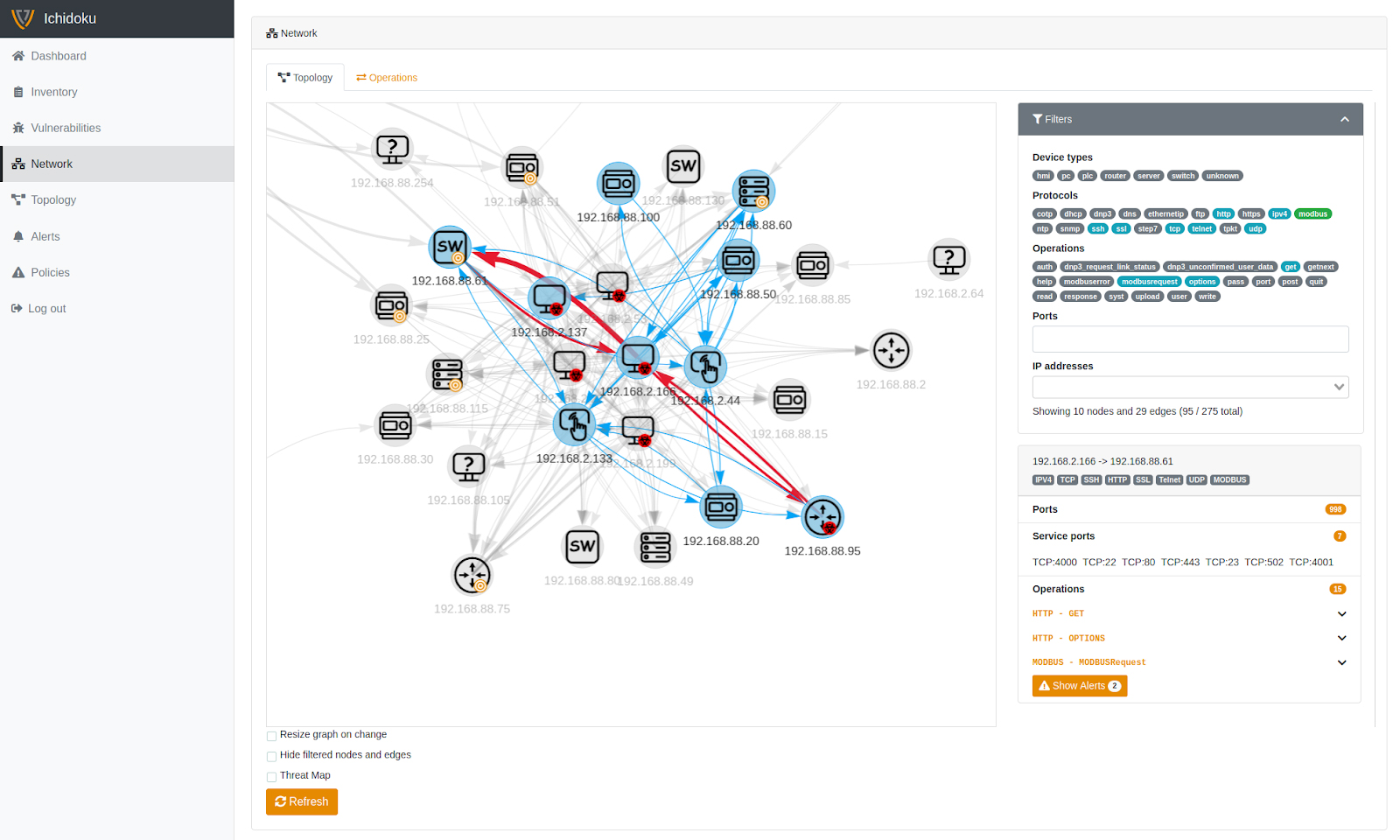
Physical and logical topology mapping
You can get an up-to-date and visible picture of existing devices in the network, physical and logical relations between them - even if they were implemented by different vendors. Furthermore, you will get real historic data of events which is extremely helpful when something unforeseeable happens. This way it is easier to identify vulnerability zones and to take appropriate precautions like regulating communication between zones or applying firewalls. With a simple drag ‘n’ drop method you can expand or shrink the provided topology map, drill down to get a specific information, use filters to your liking and better understanding.
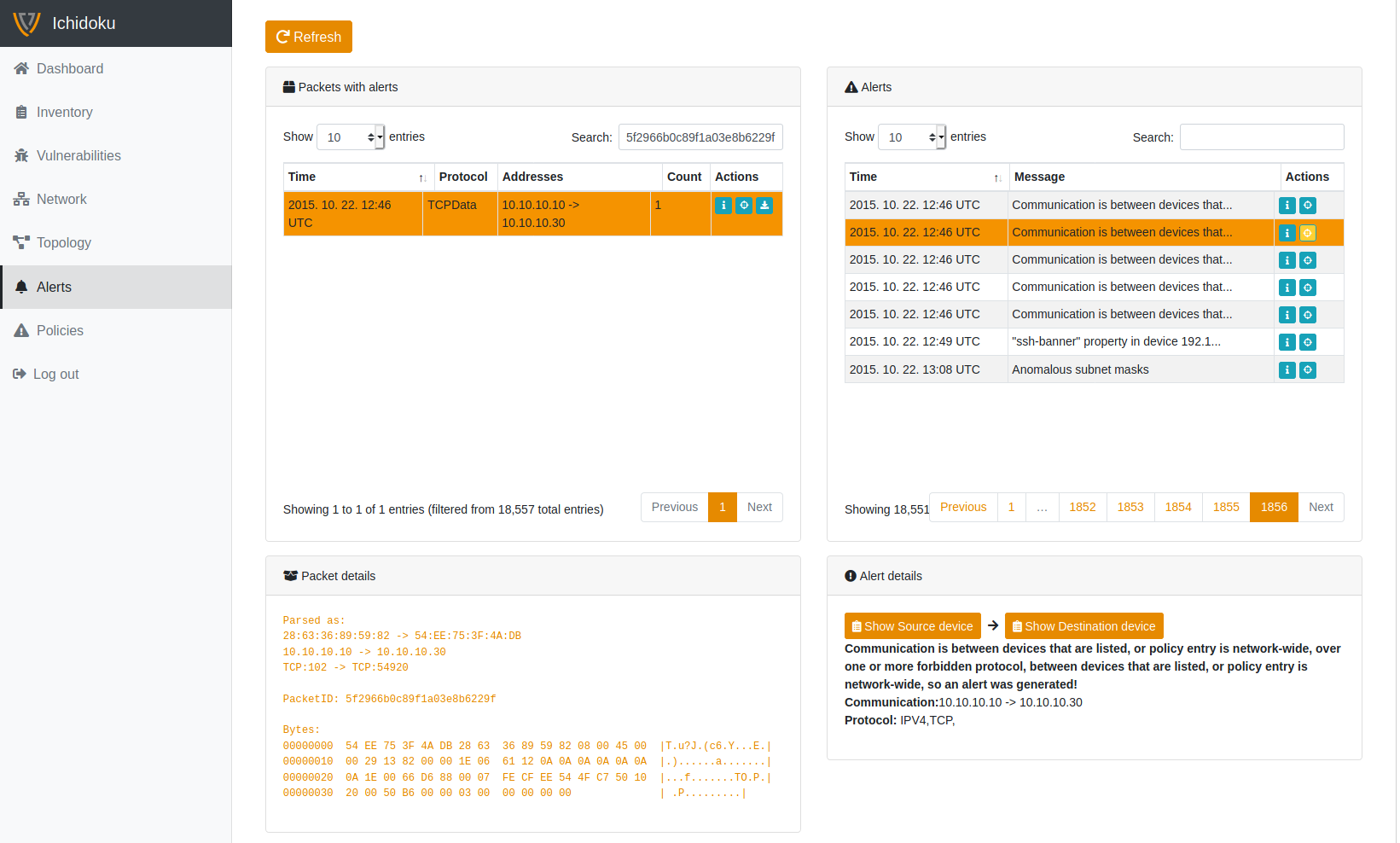
Policy based anomaly detection
Constant awareness does not necessarily require constant testing. Ichidoku comes with a built-in set of rules (based on the MITRE ATT&CK framework, and is prepared to satisfy all the needs of the IEC62443 standard) and alert function. Also, new rules can be defined with simple drag ‘n’ drop, so your internal rules will be taken to a count, and specific system needs will be met: detect insider misuses, check compliance adequacy, protect against hackers. As a bonus feature, IT and OT systems can be handled on the same interface with Ichidoku, this provides a holistic picture of a very complex environment, thus minimizing the impact of a possible attack.

Log generation
Since many industry-sized systems cannot yet generate logs (or at least some parts of it), Ichodoku comes in handy here too. Ichidoku generates logs about network events, so when an incident occurs, every detail can be tracked. Data is generated in common event format, can be stored within Ichidoku or be transferred to a classic SIEM system and correlated to the already existing logs.